CMMC Compliance: Scope, History, and Why All The Buzz?
by Serena Raymond on Aug 3, 2021 12:00:00 AM
Why is everyone talking about CMMC compliance?
You see it everywhere. What CMMC level do you need? Are you compliant? How is this related to NIST compliance? A lot of companies who don’t even need to follow CMMC compliance are worried about CMMC compliance.
So let’s get into what CMMC compliance is and why everyone is losing their head over it.
What is CMMC?
CMMC stands for Cybersecurity Maturity Model Certification. Its goal is to protect Controlled Unclassified Information (CUI). It is an audit you need to prepare for if you intend on becoming a DoD (Department of Defense) contractor, though it may extend to other government contractors as well. At the moment, CMMC is staggering their rollout of CMMC compliance.
By 2026, all companies looking to become vendors for the DoD will need to be CMMC compliant. So even if you’re just looking to bid, you will need to prove compliance. You cannot bid now and become compliant later.
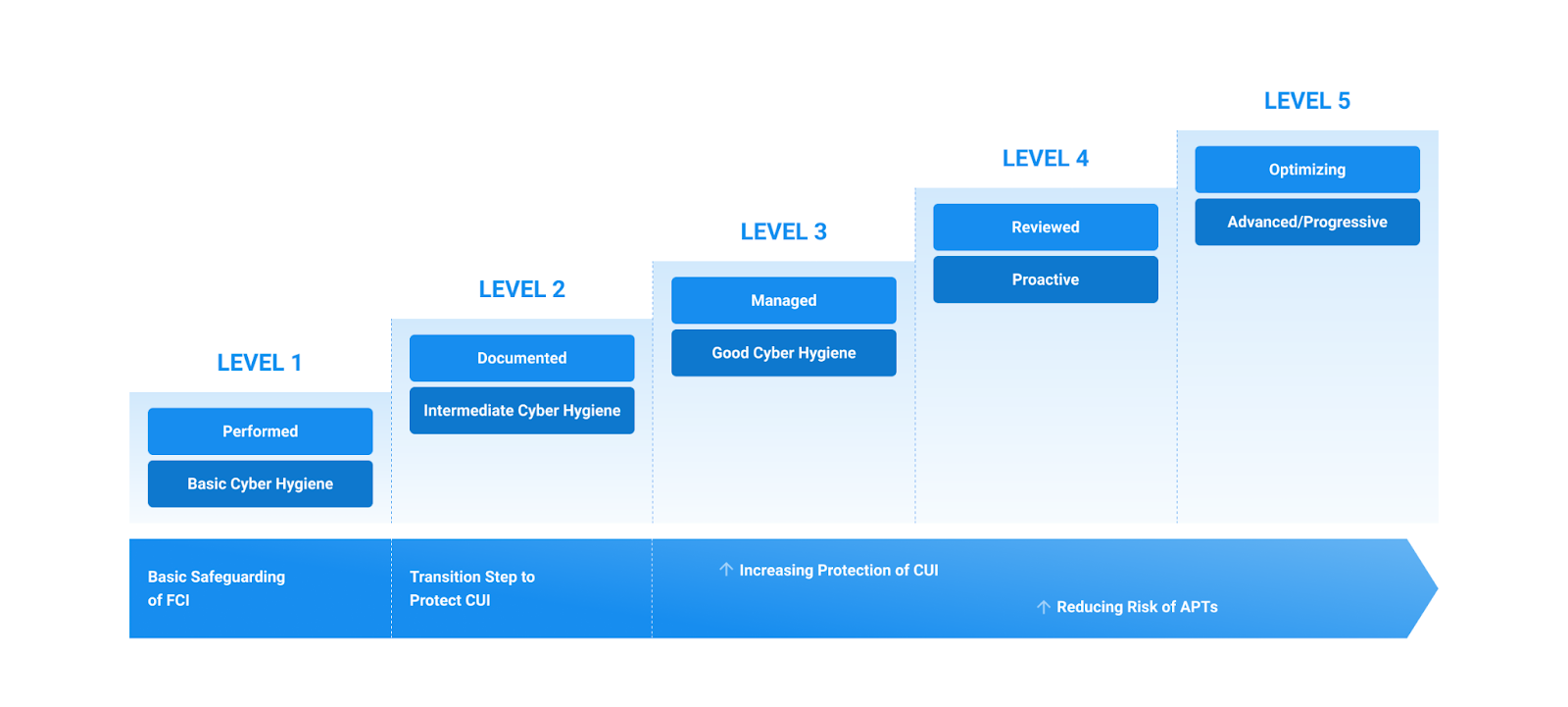
There are 5 levels under the CMMC:
- Level 1: Basic cyber hygiene
- Level 2: Intermediate cyber hygiene
- Level 3: Good cyber hygiene
- Level 4: Proactive
- Level 5: Advanced/Progressive
Each level has its own requirements and expectations, and compliance with the CMMC is all about achieving compliance with whatever level is required of your organization. Different types of companies are responsible for achieving compliance at different levels of the CMMC.
Where did CMMC come from and why does everyone seem to care?
With CMMC going into effect officially in early 2021, interest (and panic) ensued. But the CMMC goes back even further. As noted by Jacob Horne in May, the concept of CUI began in 2010 with an executive order. NARA (National Archives and Records Administration) created a CUI registry, which are roughly 20 categories that need to be protected. This took NARA 6 years. Also during this time, NIST was created and protection requirements shifted to becoming risk-based.
It was after an Inspector General report done at the congressional level came back that organizations that had implemented government frameworks were still not meeting cybersecurity standards.
After that Inspector General report was released, the Cybersecurity Maturity Model Certification was first announced in the late spring of 2019. The goal was to increase the security posture of the Defense Industrial Base (DIB) and the supply chain in particular.
In many ways, the CMMC is a synthesis of various other cybersecurity standards. In fact, Levels 3 and under of both CMMC and NIST are basically identical, they’re just called different things. More on how the CMMC relates to NIST found here.
Part of why CMMC has such a spotlight on it is because the DoD did not do a great job of explaining why they are releasing new requirements when existing frameworks such as DFARS and NIST exist. It also seemed to come out of nowhere, which is not the case at all. This has been years in the making. But because there has been a mystery surrounding CMMC, it’s spawned panic.
And there seems to be the belief that the CMMC is something everyone should follow—and that is simply not the case.
Do I need to become CMMC compliant?
That is up to you and your company. For many companies, the answer is “No.” This is a requirement for government contractors.
With that said, if you plan on seeking DoD contracts, you should start achieving CMMC compliance now.
For companies that are in vulnerable sectors (such as financial institutions, manufacturing, and professional services), it will likely make sense for you to achieve a high level of CMMC compliance as long as you have the resources. If you’re strapped for resources, don’t attempt to implement everything needed for Level 5 CMMC compliance. Instead, stick to the basics.
Similarly, if you’re not seeking DoD contracts or in vulnerable sectors, the CMMC is a great model to use to gauge your cybersecurity maturity—not something to take literally. The bigger any company gets, the more cybersecurity protections you will need in place. You need to start with building a foundation as opposed to going for the most “advanced” protections first. And that seems to be something many companies are confused about: Just because advanced protection is recommended doesn’t mean you should skip the basics.
If you have questions on cybersecurity maturity, we co-wrote this whitepaper with Huntress all about it.
PDNS and other foundational cybersecurity concepts
CMMC compliance, outside of its intended use, is a very good guidebook for how companies should scale their cybersecurity as they grow. But if you’re still at the beginning, here are the foundational concepts that you need to implement as soon as possible:
PDNS
Protective DNS (often referred to as PDNS) examines your DNS queries and implements safeguards to prevent you from accessing malicious sites that contain malware, ransomware, phishing attacks, and other dangerous content. It’s the best barrier for catching a large portion of threats. One recent study by Global Cyber Alliance found that over 33% of all threats analyzed could have been mitigated with DNS protection—that’s just a single layer that can protect companies from over one third of breaches.
PDNS is easy to implement and makes a big impact on your cybersecurity posture.

Continue reading about PDNS.
Training, MFA, and more
Aside from PDNS there are a few necessities that you should employ. Firewalls and antivirus solutions are a no-brainer at this stage in network security. You should also continue to train your employees as often as possible. Knowing the difference between a threat and a real site is a helpful tool for them to have.
You should also make MFA or 2FA mandatory wherever possible (something you can deploy with DNSFilter). And don’t forget to use a password manager!
 Guest Wi-Fi Security: Protecting Enterprise Hotel Networks
Guest Wi-Fi Security: Protecting Enterprise Hotel Networks
Guest Wi-Fi has become one of the most visible expressions of a hotel brand. Guests may never see the infrastructure behind it, but they feel it instantly when it works and just as quickly when it does not. Connectivity now sits alongside comfort, service, and location as a core part of the hospitality experience.
 The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
With the Super Bowl and 2026 Winter Olympics coinciding, all eyes have been on the world of sports in February. And with that comes some unfortunate realities: Scammers take advantage of seasonal events like this every way they can.

