Share this
NIST Compliance: Is DNS a NIST Requirement?
by Serena Raymond on Oct 26, 2020 12:00:00 AM
Companies seeking to do business with government agencies like the Department of Defense (DoD), General Services Administration (GSA), and NASA need to achieve NIST compliance. Being out of compliance with NIST 800-171 could mean losing a major government contract, finding yourself in breach of an existing contract, and in a worst-case scenario fraud.
Even if you were previously compliant, you may be out-of-compliance with NIST because of changes made in fall 2020. Since the change, we’ve received multiple questions around the DNS portion of NIST compliance.
Here, you’ll get an overview of NIST and an answer to the question: “Is DNS filtering software a requirement for NIST?”
A quick overview of NIST 800-171
NIST 800-171 is all about protecting “Controlled Unclassified Information (CUI).” These “requirements apply to all components of nonfederal systems and organizations that process, store, and/or transmit CUI, or that provide protection for such components.”
CUI is broadly defined and has multiple categories. But in the context of NIST 800-171, it refers to Controlled Technical Information. This specifically relates to technical data or computer software impacting military or space applications that are not publicly accessible and need to be controlled in some form. It can apply to engineering drawings, technical reports, documented processes, manuals, code, computer software, and more.
How does CMMC fit in?
CMMC (Cybersecurity Maturity Model Certification) is an audit you need to prepare for prior to becoming a DoD contractor. Since September 2020, CMMC is now a requirement under the Defense Federal Acquisition Regulation Supplement (DFARS Case 2019-D041), which officially goes into effect November 30, 2020. The catch is that DFARS also requires NIST 800-171 compliance. So they’re all connected, and if you’re trying to land a government contract with your IT services, you essentially need to be compliant in all three.
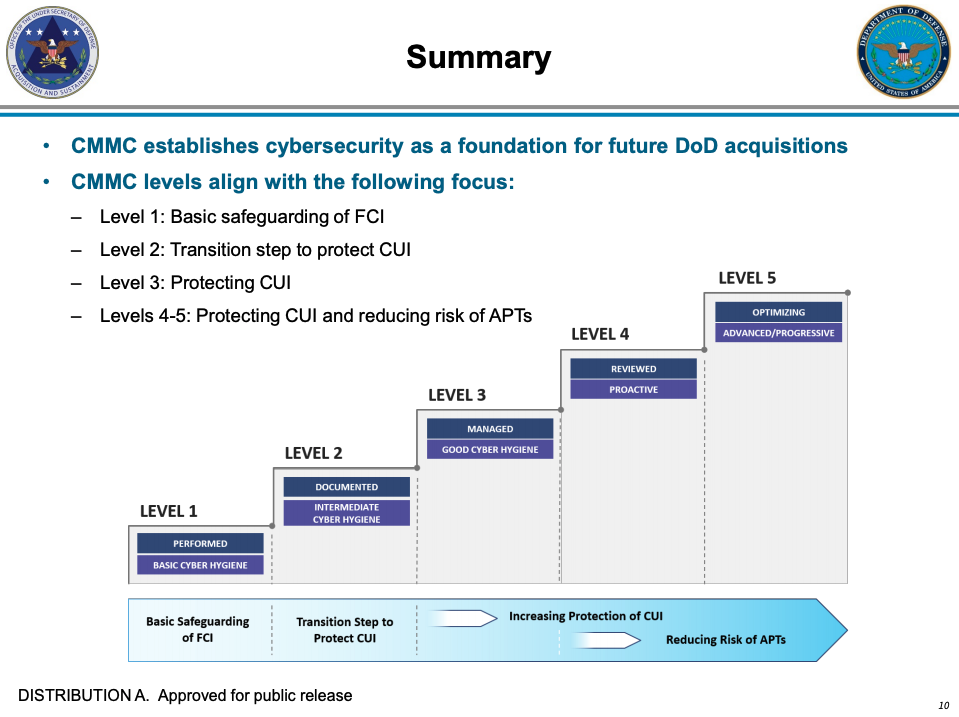
There are 5 levels under the CMMC:
- Level 1: Basic cyber hygiene
- Level 2: Intermediate cyber hygiene
- Level 3: Good cyber hygiene
- Level 4: Proactive
- Level 5: Advanced/Progressive
Each level has its own requirements and expectations, and compliance with the CMMC is all about achieving compliance with whatever level is required of your organization.
However, CMMC compliance does not equal NIST compliance, and vice versa. NIST has its own list of requirements, and while CMMC is part of that, following one does not mean you are in compliance. To achieve compliance, you need to make sure you’re following the requirements of the agency you’re working with.
Even if a contractor does not handle CUI, they will still get audited.
But…is a DNS filtering solution required?
If you’re looking to reach Level 3 of the CMMC (which would encompass 100% of NIST 800-171 CUI requirements and more), yes.
Level 3 of the CMMC is all about protecting CUI. And if you remember, the original intent of NIST 800-171 is to control CUI. While not included in the NIST controls, you must have DNS filtering to achieve CMMC Level 3. Getting to Level 3 is the safest way to make sure you’re in compliance with NIST 800-171.
According to SC.3.192 of the CMMC, vendors should “Use Domain Name System (DNS) filtering services to help block access to known malicious domains…A commercial DNS filtering service can be used.”
Implementing DNSFilter will help you achieve both CMMC Level 3 and NIST compliance. But DNSFilter doesn’t only block the known threats referred to in the CMMC. Using AI, DNSFilter will catch 0-day threats that have never been seen before, giving you a better level of protection than other filtering solutions that just upload a list of threat feeds.
What else?
Do your own research as you prepare for the CMMC audit and NIST 800-171 compliance. Document everything. Reach out to the vendors you’re using with any questions you might have about their processes and if their technology is in compliance with NIST 800-171, CMMC, and DFARS. And once you’re in compliance, don’t forget about maintaining compliance. It’s not enough to get there. Compliance is ongoing!
For additional help on what is and isn’t required, we recommend taking a look at this Compliance Forge article.

Share this
 The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
Staying Ahead with Smarter Web Filtering
Across every industry and network environment, content filtering isn’t just a matter of productivity, it’s a front line of defense. From malware and phishing to compliance risks and productivity drains, the threats are real, and the stakes are high.
 Smarter DNS Policies: What You Should Be Blocking (But Probably Aren’t)
Smarter DNS Policies: What You Should Be Blocking (But Probably Aren’t)
DNS filtering is a foundational layer of defense and helps to fortify the strongest security stacks. Most organizations use DNSFilter to block the obvious: malware, phishing, and adult content. That’s a great start, but many are missing out on the broader potential of DNS policies.
 Educating Your Clients on the Sophistication of Phishing Attacks
Educating Your Clients on the Sophistication of Phishing Attacks
Imagine losing $31,583 every minute. That’s how much cybercrime cost American businesses in 2024, according to the FBI’s Internet Crime Complaint Center. Phishing was one of the top threats behind that number. If you're still thinking phishing is just about misspelled emails from a Nigerian prince, you're dangerously underestimating today’s threat.


