DNS Encryption
by Fikayo Adepoju on Aug 25, 2021 12:00:00 AM
What is DNS Encryption
DNS is the phonebook of the internet helping users map human-readable names like example.com to IP addresses. Similar to phonebooks, all information involved in a DNS query is in plain text.
This makes it easy for anyone connected to the network, and with the right equipment, to see the DNS traffic and manipulate it or use the information for malicious purposes.
The solution to this vulnerability is what DNS encryption is all about. DNS encryption helps convert the plain text DNS information into an encrypted format that can only be decoded by the parties involved in the communication, i.e the DNS client (your browsers, network devices, etc) and the DNS resolver.
With DNS encryption in place, even if an attacker can get hold of the DNS information, they will be unable to make sense of it thus protecting you from any malicious intent.
How can DNS be encrypted?
At the moment, there are two main strategies for encrypting your DNS communication, DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH). Both solutions make use of Transport Layer Security (TLS).
In TLS, the client requests the server to set up a secure connection by performing an authenticated handshake with the server. Once the handshake is made and a secure channel is established, the client and server can then communicate by sending encrypted messages back and forth.
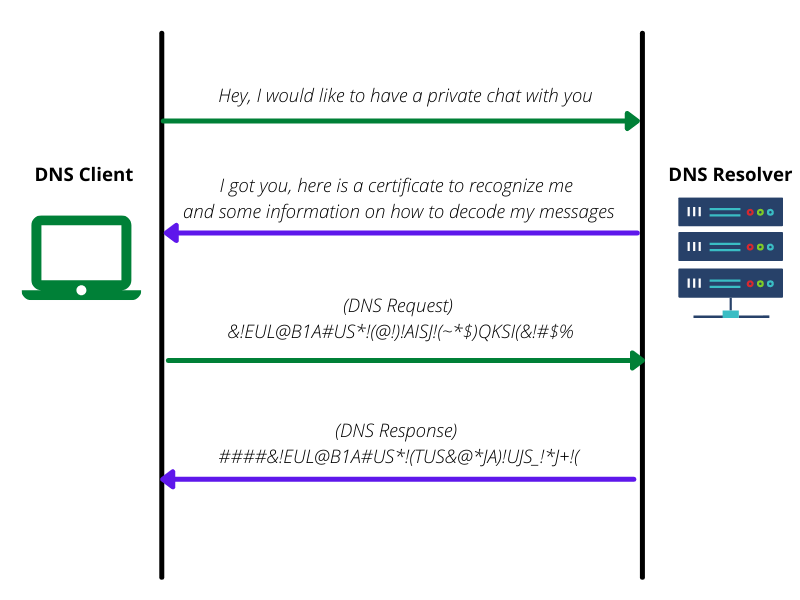
This way, the DNS client is sure that it is communicating with the right resolver (DNS server) and not some man-in-the-middle trying to snoop on the network traffic.
Let’s take a look at the two encryption strategies in more detail.
DNS over TLS (DoT)
DNS-over-TLS (DoT), released in 2016, is the first DNS encryption solution to be established.
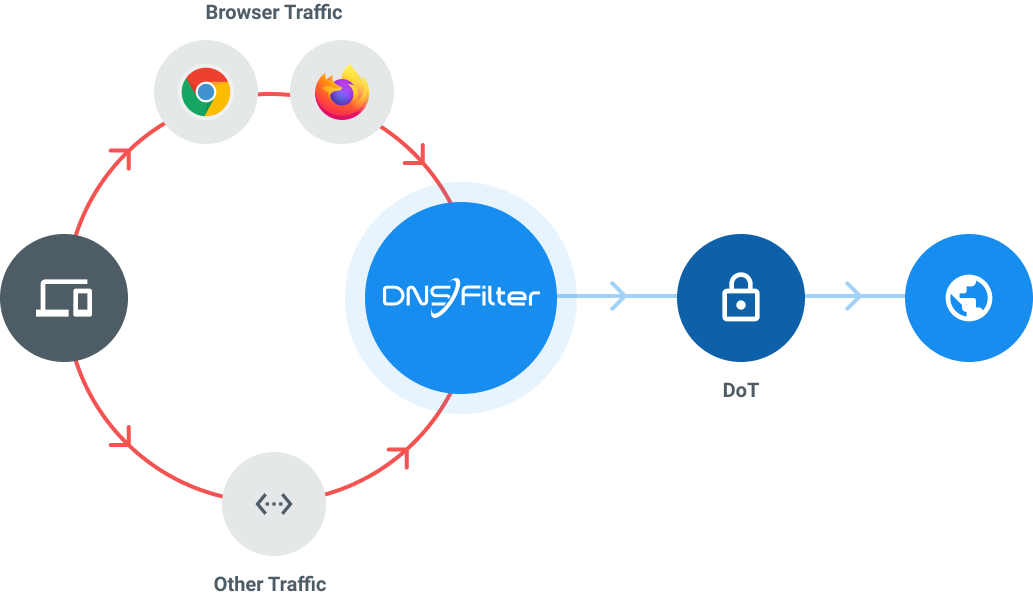
DoT channels the original client requests through a secure TLS channel on port 853 instead of the common port 53 used for unencrypted DNS communication. This prevents attackers from seeing or manipulating information about the DNS request.
Once an authenticated handshake is made and a secure channel is established with the DNS resolver, the DNS client and resolver can start exchanging messages over a secure channel. The secure connection created is mostly persisted for other DNS requests that the client will need to make during that session.
DNS over HTTPS (DoH)
The newer alternative to encrypting DNS traffic is DNS-over-HTTPS (DoH). DoH was introduced in 2018 and even though it uses TLS to encrypt messages between the client and the DNS resolver, it uses a different strategy.
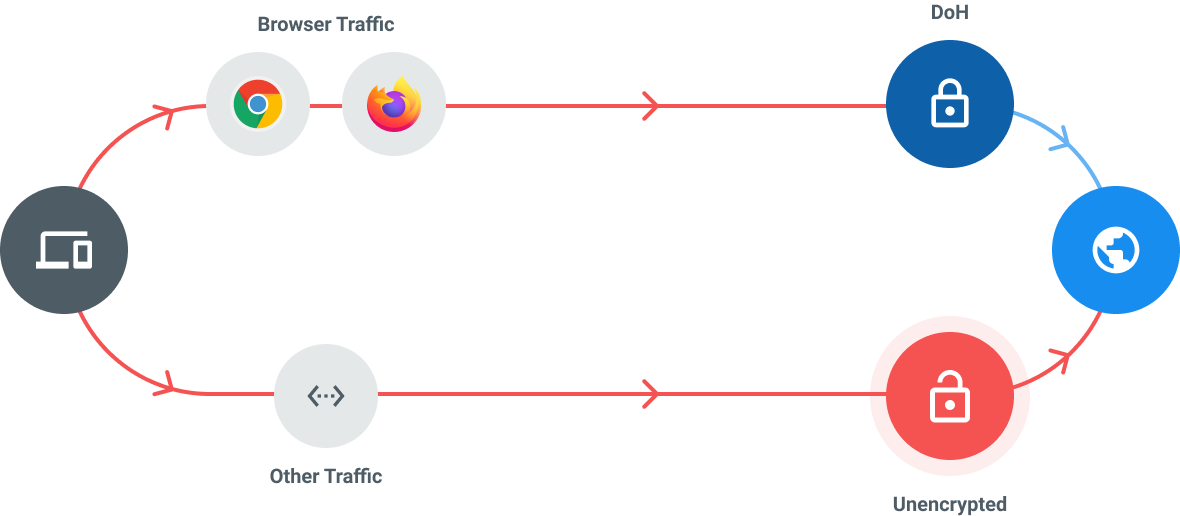
Instead of opening a new port for secure communication, it uses the same port 443 used for HTTPS requests to send a DNS query to a DNS server that supports DoH. The DNS query is sent encrypted just like a regular HTTPS request and the response is also encrypted. The client decodes the response which contains the DNS information required to reach the site.
This strategy also prevents the avoidance of DNS encryption by devices that block ports used for secure DNS communication.
Differences between DoT and DoH
Before making any strong decisions on which DNS encryption method to go with, pump the brakes for a minute as we take a look at the major differences between these two solutions:
| DoT | DoH | |
|---|---|---|
| Port | Opens a new port (853) for creating a secure connection for encrypted communication | Reuses the HTTPS port 443 for encrypted communication |
| OSI Layer of operation | Encrypted communication takes place at the Transport Layer (layer 4) of the OSI model | Encrypted communication takes place at the Application Layer (layer 7) of the OSI model |
| Operating System / Application Coverage | It is either supported natively or can be configured for various operating systems (macOS, Windows, and Linux). Once in place, it encrypts DNS communication for any application that uses DNS on the operating system. | Needs to be configured for each application/client that needs to use it (e.g. browsers like Firefox, Google Chrome, Opera, etc) |
| Packet Size | Because it operates at a lower level, its packet sizes are light | Packet sizes are larger than DoT because it operates at the Application layer (two layers above DoT) |
| Latency | Minimal latency in DNS requests | Higher latency compared to DoT |
From the table above, it is clear that DoT has a slight edge ahead of DoH mainly due to its widespread encryption coverage when implemented on operating systems and smaller footprint. Privacy is the only real benefit to DoH and it has a major downside in its requirement to be configured on every single client that wants to make use of it. For more information on comparisons between these two solutions, you can check out this article.
Conclusion
The encryption strategy you decide to go with will eventually be based on what you want to encrypt and where. The adoption of DoH is fast rising with Google being a huge contributor to that. So, it won’t be surprising to see the adoption of DoH across operating systems rise in the coming years.
No matter the solution you choose to go with, one thing is certain and that is you need to protect your DNS traffic from malicious eavesdropping. Start encrypting your DNS traffic with a free DNSFilter account today.
 Guest Wi-Fi Security: Protecting Enterprise Hotel Networks
Guest Wi-Fi Security: Protecting Enterprise Hotel Networks
Guest Wi-Fi has become one of the most visible expressions of a hotel brand. Guests may never see the infrastructure behind it, but they feel it instantly when it works and just as quickly when it does not. Connectivity now sits alongside comfort, service, and location as a core part of the hospitality experience.
 The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
With the Super Bowl and 2026 Winter Olympics coinciding, all eyes have been on the world of sports in February. And with that comes some unfortunate realities: Scammers take advantage of seasonal events like this every way they can.

