DNS Poisoning
by Fikayo Adepoju on Oct 26, 2021 12:00:00 AM
What is a DNS Poisoning attack?
In a DNS poisoning attack, also known as DNS cache poisoning or DNS spoofing attack, an attacker takes advantage of known vulnerabilities within the domain naming system (DNS) to insert a false entry into the DNS records. The attacker then uses the false entry inserted into the DNS cache to route traffic intended for a legitimate domain to a fake one.
Most of the attacks on DNS are aimed at spoofing the response to a DNS query. When an attacker is able to add a false entry to a DNS client or server’s records, the DNS record is said to be poisoned.
The term “poisoned” is used because the false entry (the poison) is injected into the system at a single point and can spread throughout the system, affecting other points.
To better understand how attackers execute a DNS poisoning attack, it’s important to first understand how DNS works. If you already have a strong understanding of DNS, its purpose, and how it operates, you can skip to the section “How is DNS poisoning done?”.
What is DNS and how does it work?
Computers work with numbers and are uniquely identified on an interconnected network using special numeric identifiers known as IP (Internet Protocol) addresses. Humans, on the other hand, are better at identifying objects with names.
For humans to effectively use the internet to identify and communicate with computers hosting the resources they need to access, there has to be a way to map human-readable names to the IP addresses used to identify computers on the network.
In comes the Domain Name System (DNS), often referred to as the phonebook of the internet. A phonebook helps to get a person’s phone number when you know the person’s name. DNS works similarly by helping humans use names that map directly to IP addresses of computers on the internet to locate the servers they want to communicate with. DNS is the backbone of the internet as it makes the internet usable for humans.
Let’s simplify how DNS works even further. DNS essentially consists of two main parts:
- A database that stores the mappings of names to IP addresses
- A protocol to communicate with the database
A computer that hosts this database and supports the communication protocol is known as a DNS server.
An entity that communicates with the DNS server by sending a name to be resolved to an IP address is known as a DNS client.
DNS servers and clients often cache resolved queries to improve the speed of the name resolution process.
A DNS operation occurs in the following steps:
- A DNS client (e.g. your browser) sends a name to a DNS server to resolve to an IP address, this is known as a DNS query
- The DNS server checks its records for an entry that matches the domain name in the query
- Once a match is found the DNS server pulls the IP address for that name from its database and returns a response to the DNS client
- The DNS client or server can decide to cache this response so that subsequent queries can be faster
As I said earlier, this is a highly simplified look at DNS and how it works; however, with this understanding, you will better comprehend how a DNS poisoning attack is implemented and how it can be very dangerous to end users.
How is DNS poisoning done?
DNS poisoning or spoofing is done when an attacker intercepts a DNS request and sends a fabricated (poisoned) response to the client.
Imagine you’re at the airport waiting for your flight, the flight is in a couple of hours, so you decide to burn some time by checking up on your Twitter feeds. You see that the airport has free WiFi, and you naively connect to it.
Unknown to you, the WiFi is insecure and an attacker has taken advantage of its loopholes to poison the DNS cache and redirect all requests for twitter.com made on the network to their machine.
You visit the domain twitter.com and the attacker redirects you to a spoofed version of Twitter that looks exactly like the original. You’re taken to the login page and you submit your credentials giving away your Twitter account to the attacker. Once the attacker harvests your login credentials, they redirect you to the original Twitter website to continue your session.
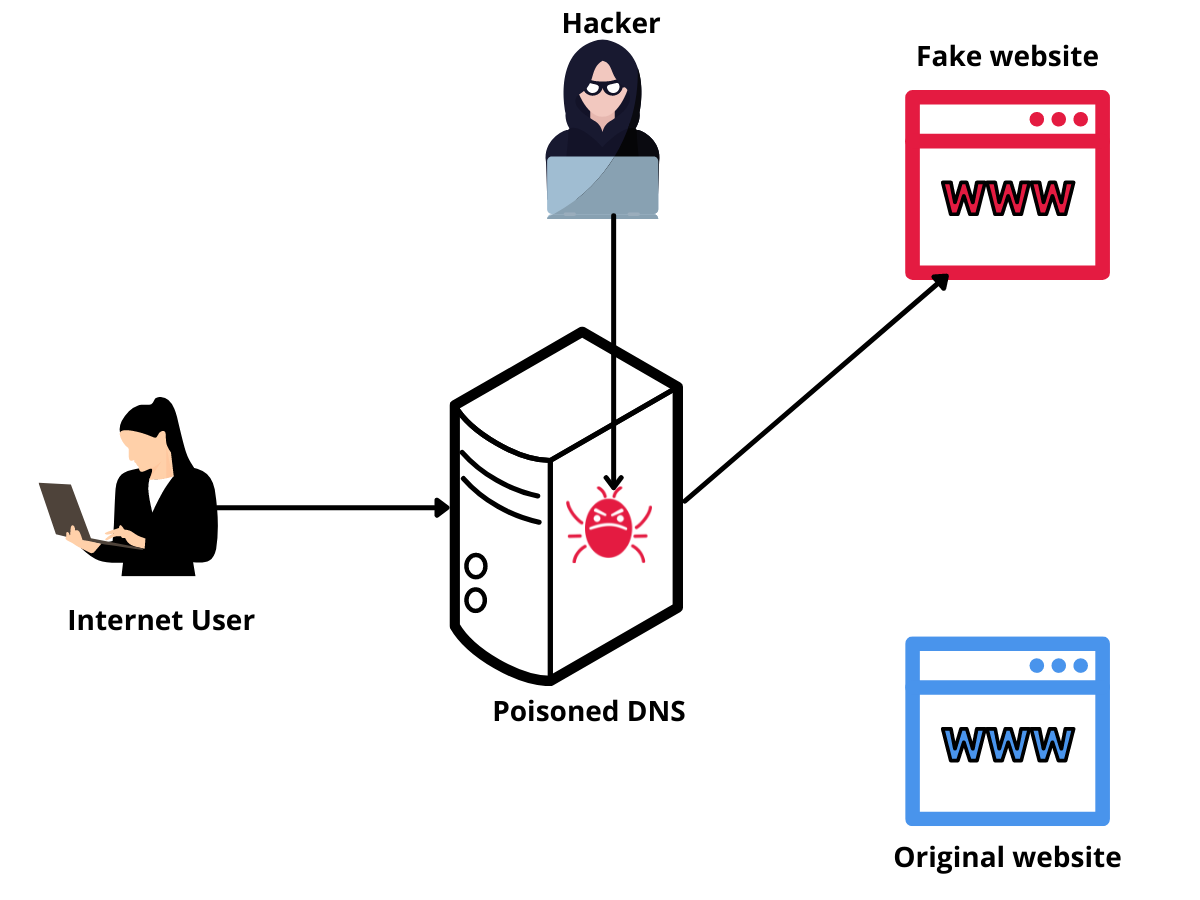
And just like that, you’re a victim of DNS poisoning.
The Domain Name Systems’ (DNS) design favors speed and scale over security, which is why it uses the User Datagram Protocol (UDP) protocol and encourages caching. This vulnerability makes it attractive to attackers as there isn’t any validation or verification system built-in. With no validation or verification, it’s difficult to verify the source and the integrity of data moving through the network in a DNS resolution process.
DNS poisoning can be done on both the client and the server-side.
Typically, DNS cache poisoning is done on the client-side. The attacker poisons the client’s DNS cache with false entries and can spoof any DNS entries they want. A DNS client in this case can either be a standard DNS client or a recursive DNS server.
On the server side, DNS poisoning can be done in two ways.
First, an attacker might intercept all requests at the DNS server and spoof the DNS responses.
A second strategy is to poison the server itself by changing the records (DNS cache poisoning); the server will then automatically direct the user to the illegitimate IP address—even after the issue is resolved.
Attackers can also perform DNS poisoning on a large scale by poisoning the authoritative DNS server for a domain. Every time a request is made for the domain from anywhere around the world, the poisoned record is returned to the client.
Once a DNS poisoning attack is in full effect, the attacker can use the opportunity for nefarious activities like stealing sensitive information (bank logins, social logins, etc.), redirecting traffic to gambling or advertising sites to promote whatever they want, or simply denying access to the original domain causing a Denial of Service (DoS) situation.
What does DNS poisoning look like to the end user?
The most effectively implemented form of a DNS poisoning attack displays a spoofed site to the end user with no visible difference from the original. This allows the attacker to take advantage of the user’s ignorance to steal sensitive information.
When a user visits a well-spoofed domain, they see no difference between it and the original. This trust makes them supply any type of information the spoofed site requests no matter how sensitive the information is. This is the perfect scenario for hackers to steal as much information as they want.
Another way a DNS poisoning attack can appear to an end user is when the domain refuses to load. This is done by attackers to frustrate the users of a service or cause harm to the business of that service. The attacker can substitute the IP address of the original domain with one that is not publicly accessible or simply spoof a “Not Found” page.
Governments can also use DNS spoofing to implement censorship laws. For example, countries like China that do not allow the use of Facebook use DNS poisoning techniques to display a censorship page or redirect citizens to a different domain when they try to visit Facebook.
In most of these cases, the end-user will likely never know they were the victim of DNS cache poisoning.
What is the difference between ARP poisoning and DNS poisoning
Address Resolution Protocol (ARP) poisoning and DNS poisoning are both Man-In-the-Middle attacks. The main difference between these two is the addressing format used and the scale on which they occur.
While DNS poisoning spoofs IP addresses of legitimate sites and its effect can spread across multiple networks and servers, ARP poisoning spoofs physical addresses (MAC addresses) within the same network segment (subnet).
An attacker uses ARP cache poisoning (or ARP poison routing) to trick the network into thinking that their MAC address is the one associated with an IP address so that traffic sent to that IP address is incorrectly routed to the attacker. This enables the attacker to eavesdrop on all network traffic between its victims.
How to prevent DNS Cache poisoning
- DNSSEC: The Domain Name System Security Extensions is a security system that helps verify the origin and integrity of data moving back and forth in a DNS resolution process. Similar to how TLS/SSL works, DNSSEC uses a public/private key pair to cryptographically verify and authenticate DNS data.
- Disable Dynamic DNS: Dynamic DNS introduces loopholes to the DNS system by allowing any system to add a record to a zone or modify a record if the security is weak. Dynamic DNS should never be enabled for servers, only private workstation networks.
- Refuse DNS requests over open ports: One of the ways attackers discover vulnerabilities is by bombarding your DNS servers with queries to take over the server. By refusing requests over open ports, you avoid queries that can contaminate your DNS data.
- Encrypt your DNS Data: When an attacker cannot read your DNS query, they won’t know which domain you’re trying to resolve hence they won’t be able to redirect you. Encrypting your DNS data ensures that even when an attacker gets hold of it, they cannot make sense of it. There are different standard ways of encrypting your DNS data but the most commonly used ones are DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH). Read this article to find out more about DNS encryption strategies.
- Run regular system updates: Operating System manufacturers are always actively working to make sure that any security vulnerabilities identified are fixed. These fixes are often implemented with system updates and DNS is one of the components in an Operating system that should be regularly updated.
DNS poisoning is a very dangerous form of attack because it can be extremely difficult for users to detect. Attackers are getting better at making fake websites identical to the original, making it easy to steal sensitive information from unsuspecting users. According to experts, 33% of data breaches can be prevented by ensuring that the DNS layer is well protected.
To learn more about how DNSFilter uses DNSSEC to protect you against DNS poisoning, check out this article on our Knowledge Base.
 6 Security-Focused New Year’s Resolutions for 2026
6 Security-Focused New Year’s Resolutions for 2026
The start of a new year is the perfect time to reset habits—not just personal ones, but digital habits too. Cybercriminals don’t need zero-days or nation-state tooling if we keep handing them easy wins through reused passwords, oversharing, and rushed reactions.
 Inside Business Email Compromise Scams: How to Protect Your Business
Inside Business Email Compromise Scams: How to Protect Your Business
The Scam That Outsmarts Awareness Training
It starts with a routine email.



