Share this
How To Spot A Coronavirus Scam
by Serena Raymond on Apr 7, 2020 12:00:00 AM
Hackers are incredibly busy right now. Everyone is at home, working if they can, and everyone is online. It’s created the perfect moment for coronavirus scams to take center stage.
At DNSFilter, we’ve noticed a surge in bad sites detected by our AI on a daily basis beginning in February. While we can’t say for certain this 11% increase is due to deceptive COVID-19 content, the timeline matches up to when coronavirus started to become a big deal in the US.
Using confirmed coronavirus scams, we’re able to train our AI on both what a bad coronavirus site looks like and what a good coronavirus site looks like. After all, we don’t want to block users from accessing helpful resources about COVID-19.
In this post, we’ve pulled a few examples of confirmed coronavirus scams to help you identify if a site is legitimate or harmful.
An app cannot keep you from getting coronavirus
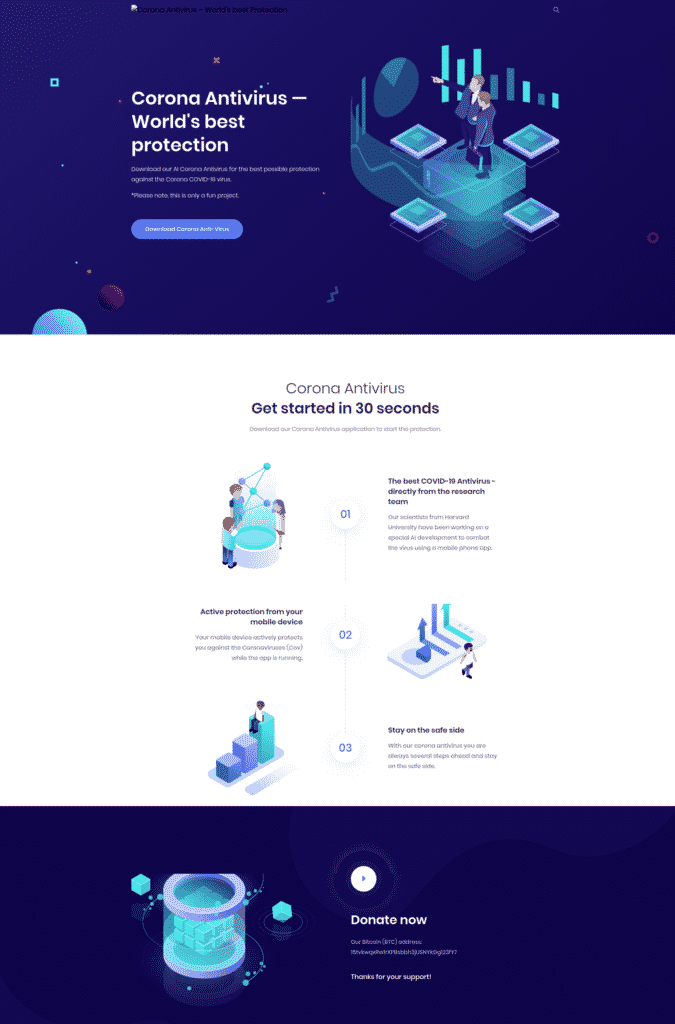
This website is pretty convincing on the surface. It has a nice layout and real graphics, but if you actually read the text of the site you’ll notice a few red flags.
First, this website is claiming that downloading a mobile app will automatically protect you from coronavirus. I don’t think you need me to tell you that, that’s just not true. But reading the fine print is important.
Also, notice the broken links at the top of the page where a logo should be.
Finally, requesting donations in Bitcoin instead of deploying to the app store and charging a fee, or even setting up a legitimate Fundly account is a little alarming. If this site was actually determined to help people, they wouldn’t be afraid to have their name on it or use trusted channels to ask for donations.
So if you see a site promising some sort of mobile app wizardry in exchange for Bitcoin, please move on from that site. And report it to the domain registrar, too, so they can take down the site.
Just because information seems helpful, doesn’t mean you should trust it
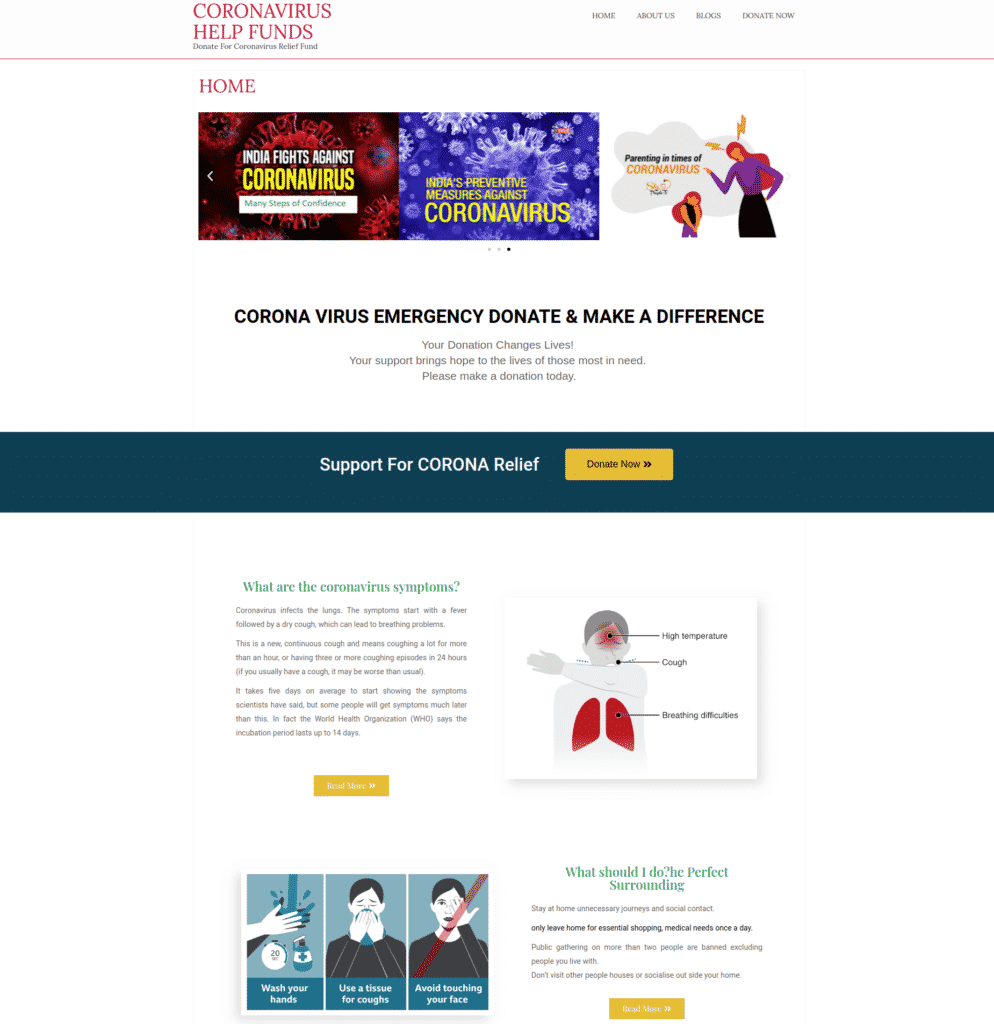
This site isn’t as slick as the first example, so it’s a little easier to be wary of it after just giving it a quick glance. There are also spelling errors and strange wording throughout the page that should be red flags. One of them is in the heading of a major callout on the page.
However, the information it’s giving is helpful. But that’s not a reason to think this site was created with good intentions.
If we click around this website, we realize only the homepage is set up. Trying to click “About us” to learn more about this relief fund links to a shell of a page.
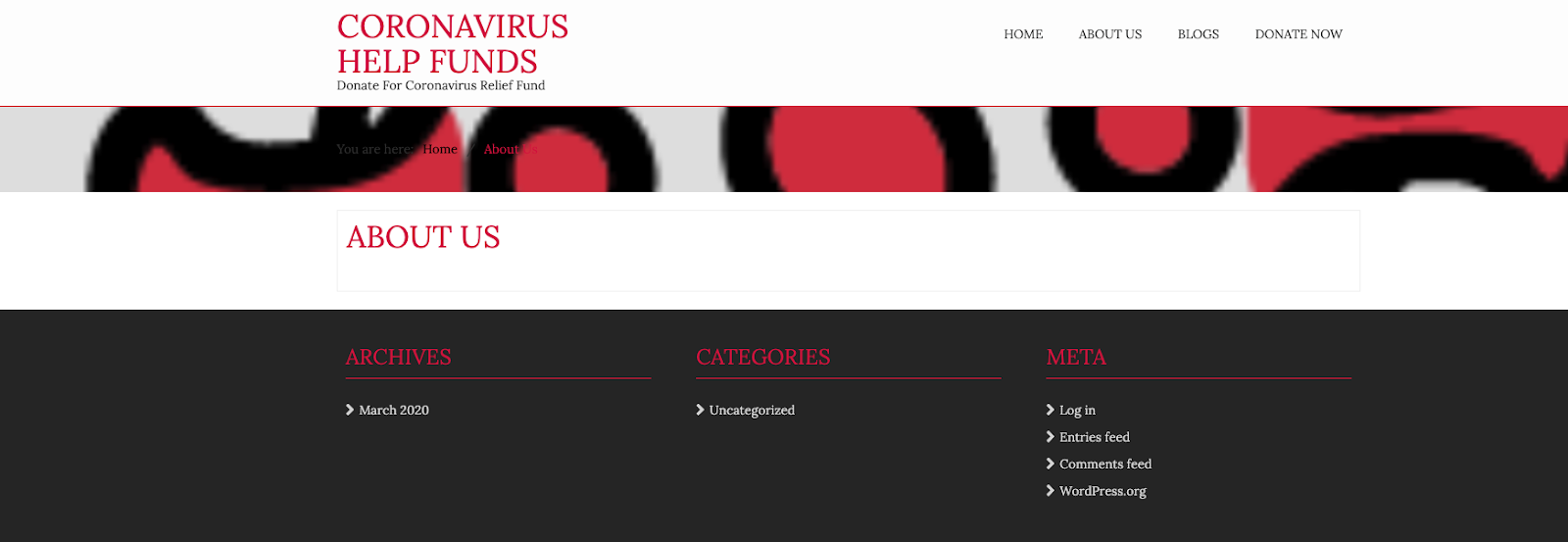
The “login” page is actually a link to the backend of the website. There are still links to the original WordPress in the footer, which is often an indicator of scam site. The hacker putting the site up wants to spend as little time as possible getting it up so they can start capturing donations. This usually means small details, like a real footer and navigation, aren’t set up.
If you see a site that looks suspiciously like very little time was spent putting it together, but they’re asking for money, don’t trust it.
The unfinished page

This particular site has even less effort put into it than the previous one. Only the images above the fold (basically what you can view when opening the page without scrolling) show anything related to coronavirus. Everything below the fold still shows images from the template this hacker used.
But just focusing on the elements this hacker wants people to care about: The images used at the top are poorly designed, and the text is hard to read.
And there is an especially devious message to the left of the donate button:
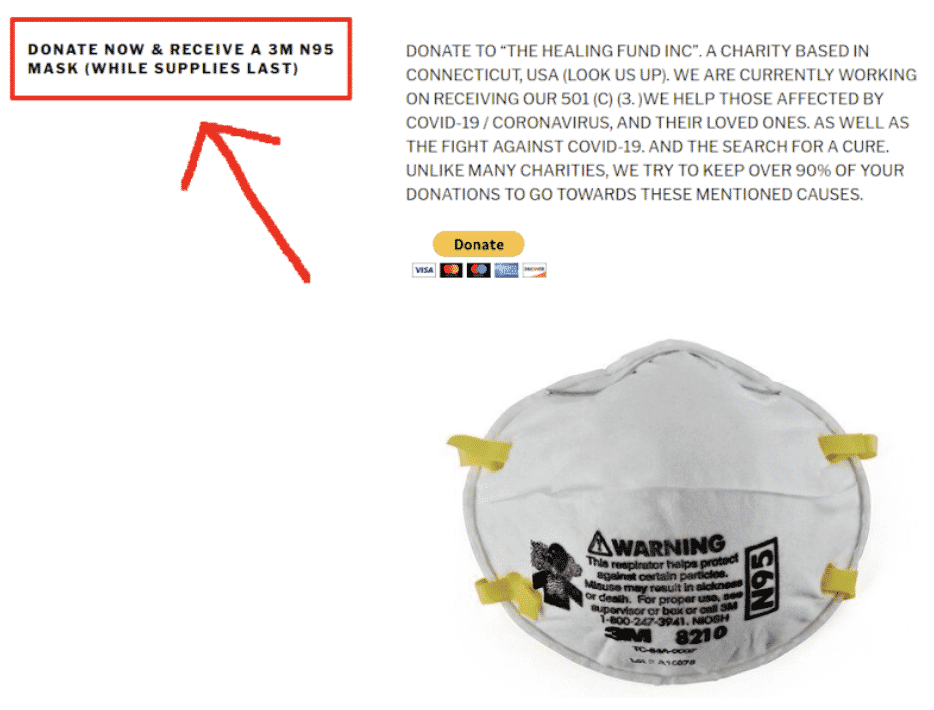
Promising people who donate a product that is currently in-demand and very difficult to obtain is a common tactic. And a lot of people are desperate enough to get their hands on something like an N95 mask to donate a few bucks to a seemingly harmless group “raising money for charity.”
Additional advice on avoiding coronavirus scams
Something you might have noticed in the previous examples is that all of these people who are working hard to help everyone affected by coronavirus are completely anonymous. There are no pictures of the people who developed the application, there is no background on the people who are raising funds, and there is no reason for why they’re choosing to get involved in this way.
Don’t trust anonymous groups like this that are seeking donations, especially when their websites provide no substantial information.
While these are scams focusing on donations, as those seem to be in high demand right now, Ransomware-as-a-service is also on the rise. Some of this malware is deployed through fake coronavirus maps, places where you might be able to get vaccinations, or home test kits.
The general recommendation here is to beware of anything that seems too good to be true. If a site is promoting a giveaway of a product that’s hard to come by right now in exchange for a donation, don’t do it.
If you want to donate to help make a difference, use sites like Charity Navigator to ensure you’re supporting real organizations with a mission. It’s natural to want to help right now, but with so many COVID-19 scams out there, we also need to be prudent about how we support causes we care about.
While the coronavirus pandemic is having us all work from home, we’ve decided to share DNSFilter free through July 1, 2020. Start your free trial.
Share this
 Shadow IT: The Hidden Threat in Your Clients' Networks
Shadow IT: The Hidden Threat in Your Clients' Networks
Shadow IT is quickly becoming one of the biggest blind spots in cybersecurity, especially for MSPs. As clients increasingly adopt cloud-based tools, browser extensions, and AI-powered applications, many of these services bypass traditional IT oversight. These unsanctioned tools may seem minor at first, but they can introduce serious vulnerabilities to your clients' environments.
 Tycoon 2FA Infrastructure Expansion: A DNS Perspective, and Release of 65 Root Domain IOCs
Tycoon 2FA Infrastructure Expansion: A DNS Perspective, and Release of 65 Root Domain IOCs
Our analysis of Tycoon 2FA infrastructure has revealed significant operational changes, including the platform's coordinated expansion surge in Spanish (.es) domains starting April 7, 2025, and evidence suggesting highly targeted subdomain usage patterns. This blog shares our findings from analyzing 11,343 unique FQDNs (fully qualified domain names) and provides 65 root domain indicators of compromise (IOCs) to help network defenders implement mo...
 The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
Staying Ahead with Smarter Web Filtering
Across every industry and network environment, content filtering isn’t just a matter of productivity, it’s a front line of defense. From malware and phishing to compliance risks and productivity drains, the threats are real, and the stakes are high.


