A Statement on the Kaseya Ransomware Attack
by DNSFilter on Jul 6, 2021 12:00:00 AM
Just before US offices closed for the Fourth of July holiday, the MSP vendor Kaseya was hit by a huge ransomware attack. The organization behind the attack is REvil, a Russian-linked Ransomware-as-a-Service operation that first surfaced in May 2020. In 2021, they have been attached to a number of high-profile attacks. This breach is still ongoing, but we want to alert our customers to the actions that we have taken at DNSFilter to best secure our customers.
We want to reiterate that if you are a Kaseya customer to follow their advice:
“Our guidance continues to be that users follow Kaseya’s recommendation to shut down VSA servers immediately, to adopt CISA’s mitigation guidance, and to report if you have been affected to the IC3.”
Initial Domain Flagged
At 3:56 p.m. ET on July 2, DNSFilter categorized the first known URL as malware after it was first posted at roughly 3:19 p.m. ET: decoder[dot]re
Prior to our categorization of this domain, there was no traffic to this domain on our network.
Config file with over 1,000 domains disclosed
Early on July 3, a config file was released for the Kaseya attack that included a list of over 1,200 command and control domains. As of 3:58 a.m. ET on July 3, DNSFilter is categorizing all of these domains as malicious.
To ensure you’re protected from these domains sending DNS queries from your system, ensure you have the following DNS threat protection in place (at a minimum) on our network:
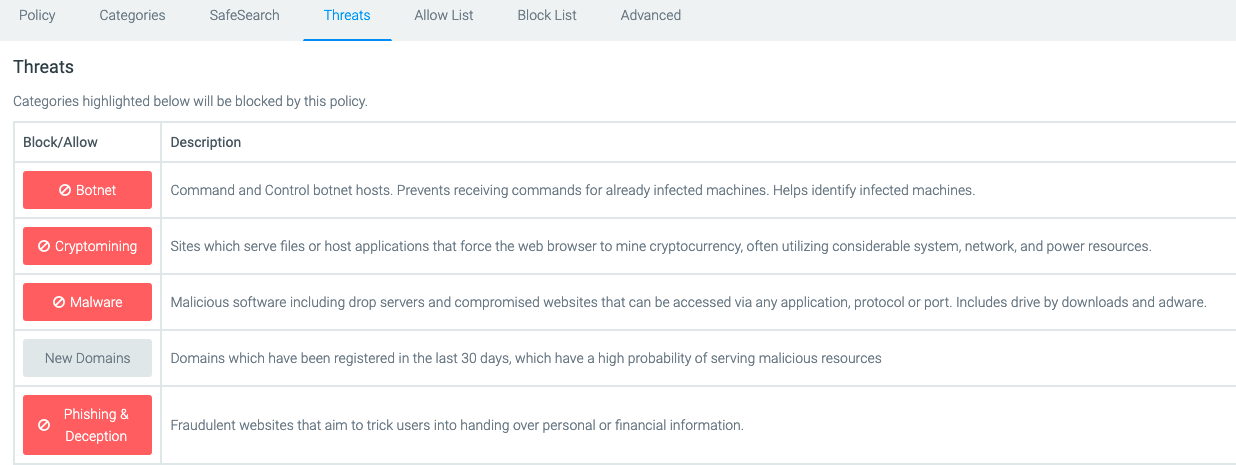
As more information is released or we have additional updates related to actions we are taking at DNSFilter to protect our customers, we will update this blog post.
Update on July 9, 2021: We have shared more information about the CNC domains used in the Kaseya ransomware attack.
 6 Security-Focused New Year’s Resolutions for 2026
6 Security-Focused New Year’s Resolutions for 2026
The start of a new year is the perfect time to reset habits—not just personal ones, but digital habits too. Cybercriminals don’t need zero-days or nation-state tooling if we keep handing them easy wins through reused passwords, oversharing, and rushed reactions.
 Inside Business Email Compromise Scams: How to Protect Your Business
Inside Business Email Compromise Scams: How to Protect Your Business
The Scam That Outsmarts Awareness Training
It starts with a routine email.



