DNS Tunneling
by Fikayo Adepoju on Aug 4, 2021 12:00:00 AM
What is DNS Tunneling
DNS tunneling is a malware technique that allows an attacker to establish a command-and-control (C2) channel to a victim’s computer. The channel created provides a means of encapsulating malicious payload within DNS queries to take advantage of the relatively unrestricted flow of DNS traffic especially in scenarios where almost all other traffic is restricted.
Another common use of DNS tunneling is data exfiltration, a process in which attackers steal information from the victim’s computer. As cybersecurity experts continue to block or heavily control other channels like FTP and HTTPS, the use of DNS tunneling is increasing.
How DNS Tunneling Works
The Attacker’s mind
The DNS service is critical for most networks and as such is typically allowed to pass through most firewalls unfiltered. The UDP port 53 most commonly used for DNS traffic cannot be completely blocked by organizations as this will break most, if not all, network communication.
Attackers fully understand this situation and have crafted various means of exploiting it, one of which is DNS tunneling. To perform DNS tunneling, an attacker infects a victim’s computer with malware which then allows the attacker to establish the C2 channel for sending information to and receiving commands from the attacker’s server.
Setting up a DNS Tunnel
To set up a DNS tunnel to a victim’s computer, an attacker registers a domain like example.com.
The attacker then proceeds to register their server as the domain’s authoritative DNS server. Oftentimes, a subdomain is also set up where the authoritative DNS server redirects the domain traffic. With this setup, the attacker can listen to the DNS port on the C2 server for DNS requests coming from the infected system.
When an infected system makes a DNS request to resolve example.com, a connection is established between the infected system and the attacker’s C2 server creating a covert channel that can be used for malicious activities like uploading and downloading files, executing programs, launching an interactive shell, etc.
How an attacker can take advantage of DNS tunneling
One of the most common uses of a DNS tunnel is data exfiltration. The infected system can use the channel created to pass sensitive data to the attacker’s C2 server. Let’s look at an example.
Imagine a victim’s computer is infected with malware and listens for keystrokes to capture the user’s username and password when they visit a particular website—let’s say their bank website.
This captured information can then be encoded in base64 and attached to the DNS query like below:
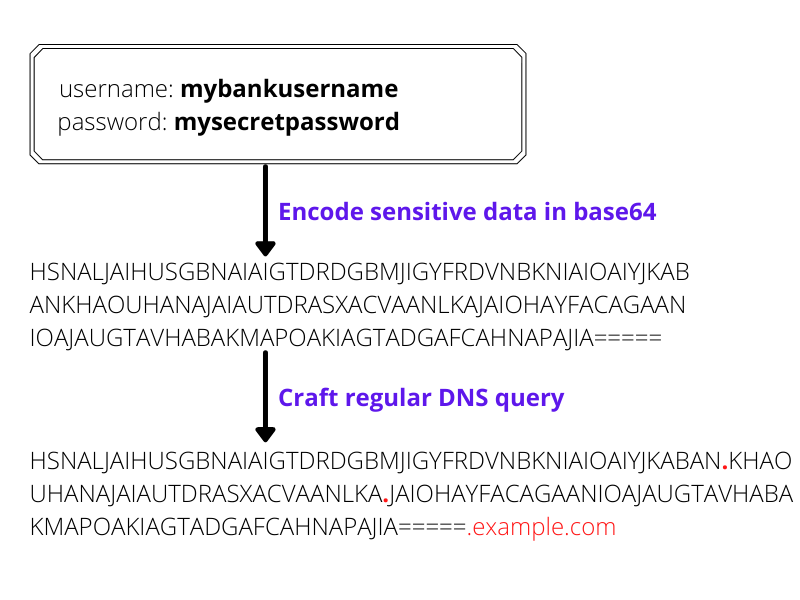
Because this string has all the characteristics of a valid DNS name, it can be sent undetected to the attacker’s computer where it can be decoded and inspected.
Just as infected zombie systems can communicate with the C2 server over the created channel, the attacker can also communicate back. Using well-crafted DNS records (A, AAAA, TXT, etc) in the query response, an attacker can send a command back to the malware on the victim’s computer to perform more tasks e.g., install additional malware, shut down the victim’s computer, encrypt the victim’s hard drive and request ransom, etc.
Another use of DNS tunneling is to provide heartbeat signals to the C2 server. This signal is sent from the victim’s computer to the C2 server letting the attacker know that the infected machine is still available and waiting for commands.
An attacker establishing a DNS tunnel can be compared to an ill-intentioned person gaining access into your house, there is really no limit to what they can do. The magnitude of possible damage is always based on what their evil intentions are.
Preventing DNS Tunnelling Attacks
DNS Filtering (Recommended Solution)
Having a DNS filtering system to filter your DNS requests is one battle-tested solution that can help prevent DNS tunneling attacks.
Because DNS tunneling uses DNS queries to establish a malicious connection with the attacker’s computer, monitoring, detecting, and blocking malicious queries proves to be very effective in combating these types of attacks.
Some of the features required of a good DNS filtering system are listed below:
- Detect phishing attacks that can lead to the installation of malware
- Each time a DNS server receives a DNS request, it should be compared against a block list of known malicious domains
- Detection of Domain Generation Algorithms (DGAs) used by attackers to generate random domains for attacks
- Detect and alert on unusual DNS traffic patterns
DNSFilter offers these features and more to help guard against DNS tunneling attacks. You can start with a free account today.
Other (Manual) Precautions
Aside from filtering DNS queries, there are other precautions you can take after implementing a DNS filtering solution. These include:
- Removing local admin privileges from users
- Create an “Allow list” of applications that can be installed on the system
- Installing a Host-based intrusion detection system (IDS)
- Installing Anti-malware
- ...and many more host-level protective measures.
DNS tunneling is one of the strategies used for launching Advanced Persistent Threats (APTs) on a victim’s computer. The persistence of this threat makes it more dangerous as it can live undetected on a compromised system for so long exposing it to dangers only limited by the attacker’s malicious mind.
Start protecting your networks today by getting a free trial of DNSFilter. If you need more information about our DNS filtering solution, feel free to book a demo with us.
 The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
The Big Game, Olympic Mania: Navigating the Surge in Malicious Sports Betting Sites
With the Super Bowl and 2026 Winter Olympics coinciding, all eyes have been on the world of sports in February. And with that comes some unfortunate realities: Scammers take advantage of seasonal events like this every way they can.
 6 Security-Focused New Year’s Resolutions for 2026
6 Security-Focused New Year’s Resolutions for 2026
The start of a new year is the perfect time to reset habits—not just personal ones, but digital habits too. Cybercriminals don’t need zero-days or nation-state tooling if we keep handing them easy wins through reused passwords, oversharing, and rushed reactions.

