Share this
Introducing Active Directory (and more!)
by Serena Raymond on Jun 3, 2020 12:00:00 AM
After months of work and beta testing, our Active Directory integration has arrived.
The juicy Active Directory details
Now when you login to your DNSFilter account, you’ll see two new sections under “Deployments”:
You will begin your integration by using “Sync Tools.”
Navigate to the “install” tab and follow the instructions to download to your desktop. Watch the video above for more details and best practices around things like copying the site key.
Once you’ve finished your installation, go to “Collections” to add your first collection. After you create that first collection, you’ll see that all of your Active Directory groups are now synced to this section. So you select individual users or groups and create new collections.
Once you’ve created your first collection, you can apply policies and block pages from the main “Collections” page.
If you have multiple users in different collections, prioritize your collections using the drag-and-drop feature so that the most important policy is always enforced.
Active Directory is only the beginning
As we built our Active Directory integration, a lot of thought was put into other directory services that our customers are likely to need in the future. Because everyone works differently. So Active Directory (and Azure Active Directory) may be first, but it won’t be the last.
As time goes on, we’ll add more Active Directory services like Google Cloud IAM, Sambra, and OpenLDAP.
If you’re eager to learn more, we are hosting a webinar on Active Directory on Thursday, June 11 at 1 p.m. ET.
A few more goodies
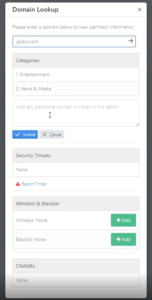
We haven’t been hard at work on just Active Directory! While that’s our big news this week, we also added new capabilities under “Domain Lookup.”
Previously, when a user wanted to report a site as a threat or label a site miscategorized, the alerts were simply sent to DNSFilter. Now, you have the option to add some notes about what you saw and why you think something is a threat.
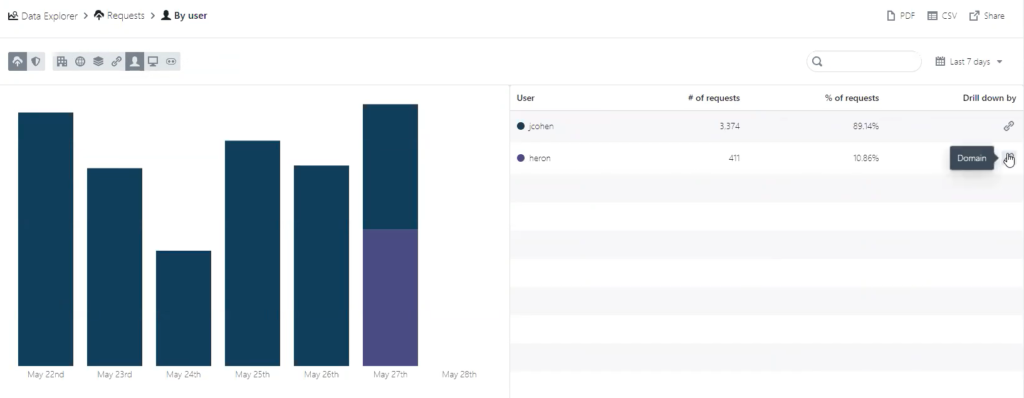
The other feature we’ve added has to do with Data Explorer. We’re continuing to make improvements to our reporting over time, and in this release we’re addressing a customer ask that we’ve seen a few times.
Customers using Roaming Clients can now drill down by domain in the user view. This enables you to see the specific domain, number of requests, and percentage of requests all by specific users using the same device.
We’re so excited to bring more functionality to our users, and Active Directory is a big step. I want to encourage everyone to keep providing feedback as you test Active Directory and other new features.
One final shoutout to our beta testers who provided invaluable feedback during the process.
Watch our Active Directory webinar
Share this
 Tycoon 2FA Infrastructure Expansion: A DNS Perspective, and Release of 65 Root Domain IOCs
Tycoon 2FA Infrastructure Expansion: A DNS Perspective, and Release of 65 Root Domain IOCs
Our analysis of Tycoon 2FA infrastructure has revealed significant operational changes, including the platform's coordinated expansion surge in Spanish (.es) domains starting April 7, 2025, and evidence suggesting highly targeted subdomain usage patterns. This blog shares our findings from analyzing 11,343 unique FQDNs (fully qualified domain names) and provides 65 root domain indicators of compromise (IOCs) to help network defenders implement mo...
 The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
The Best Content Filter Software Checklist: A Buyer's Guide to DNS-Level Protection
Staying Ahead with Smarter Web Filtering
Across every industry and network environment, content filtering isn’t just a matter of productivity, it’s a front line of defense. From malware and phishing to compliance risks and productivity drains, the threats are real, and the stakes are high.
 Smarter DNS Policies: What You Should Be Blocking (But Probably Aren’t)
Smarter DNS Policies: What You Should Be Blocking (But Probably Aren’t)
DNS filtering is a foundational layer of defense and helps to fortify the strongest security stacks. Most organizations use DNSFilter to block the obvious: malware, phishing, and adult content. That’s a great start, but many are missing out on the broader potential of DNS policies.


