Saved by the Logs: DNSFilter's Role in Stopping a Fileless Attack
When a benign PowerShell alert surfaced after work hours, most tools came up empty. But DNSFilter’s real-time logs told a different story—revealing a fileless malware attempt blocked before a single byte hit the endpoint.
The Situation
Matthew Chambers runs FixFinder, a security-focused MSP that supports high-exposure clients with a strong emphasis on security. One of those clients—a 200-employee, fully remote research firm—publishes market intelligence used by banks, insurers, and cybersecurity vendors.
Because the firm’s analysts routinely collect data from across the public web, the organization faces a persistent threat from phishing, malware, and unsafe web content. To stay ahead of that risk, FixFinder deploys three key layers of protection on every workstation: DNSFilter for AI-driven threat and content filtering, RocketCyber serving as the client’s managed SOC, and SentinelOne for endpoint detection and response (EDR).
Late one evening those layers were quietly tested when an analyst encountered what looked like an ordinary CAPTCHA prompt—triggering a chain of events.
“DNSFilter gave me the evidence, the containment switch, and the audit trail—all in one place. That’s how incident response ought to feel.”

Matthew Chambers
Founder, FixFinder
The Problem
It started with a single, subdued alert from RocketCyber: PowerShell execution via MSHTA—benign. Matthew had seen plenty of loud, unmistakable breaches in his career, but this understated flag felt more ominous. “On a quiet dashboard,” he says, “benign can be the scariest word in the world. If the SOC isn’t sure, I assume the worst.”
His first sweep turned up nothing else. SentinelOne showed no detections, the mail-security logs were clean, and the analyst whose laptop triggered the event hadn’t noticed anything amiss. Everything on the surface pointed to a false alarm—yet Matthew knew that a fileless attack could hide in exactly this kind of silence.
The Solution
Rebuilding the Timeline with DNS Logs
A single RocketCyber alert raised the flag, and while Matthew isolated the activity from the user in SentinelOne, the activity from the user was a lot of noise. For example, “about 10,000 events every fifteen minutes from windows,” Matthew noted. What he really needed was a replay of the user’s web activity, something DNS is particularly good at. Matthew pivoted to DNSFilter, where real-time DNS logs exposed the web traffic and every network call that made root cause analysis possible—enabling a precise reconstruction of the attack window. By filtering the DNS logs to a tight two-minute window when the alert occurred, he quickly narrowed the view to DNS queries classified as Very New, Uncategorized, and Malware requests. Three domains leapt off the screen:
- A Greek banking site domain whose visit triggered a malicious Google ad labeled as
Uncategorized Human-verify-7u.pages[.]dev— brand-new Cloudflare Pages site less than two days hold hosting a fake CAPTCHARecaptcha-manual[.]shop— delivered the payload camouflaged as a video file; already marked asMalwareand blocked
The logs showed that the request to recaptcha-manual[.]shop originated from a PowerShell process, confirming the clipboard trick captured outside the browser.
Thanks to DNSFilter, the payload download never reached the endpoint. With the domain names in hand, Matthew called the analyst. She recalled visiting a Greek banking site as part of her research. When he showed her a screenshot of the fake CAPTCHA box from the logs, “she instantly remembered clicking it,” he said. “It seemed harmless.”
"Thanks to DNSFilter, the payload download never reached the endpoint."

Matthew Chambers
Founder, FixFinder
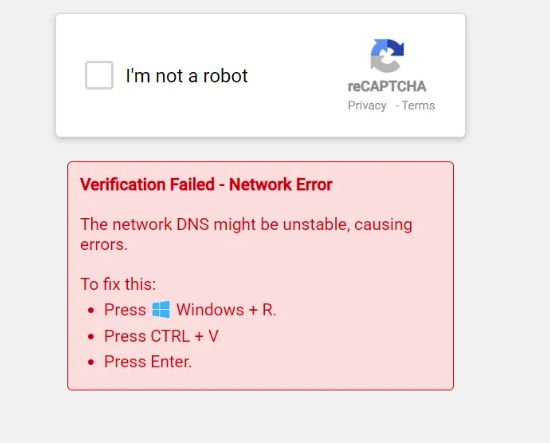
Fake CAPTCHA lure: this page claims DNS “network error” and tells the user to press Windows + R and paste a command from the clipboard, and hit Enter—steps that would silently launch the Lumma Stealer payload via PowerShell outside the browser and perform a DNS lookup.
The malware in this event was Lumma Stealer, delivered through a fake CAPTCHA in a deceptive malvertising chain. Had the analyst’s device been infected, the PowerShell payload could have disabled Windows AMSI and loaded Lumma DLL.
The stealer immediately sweeps the system for anything it can monetize—browser-stored passwords and cookies, saved 2FA tokens, cryptocurrency-wallet data, remote-access credentials, and even password-manager vaults.
Straightforward Containment
Matthew added the two domains to the customer’s global block list immediately and submitted them through DNSFilter’s Domain Report feature; within the hour they were classified as phishing by DNSFilter’s AI, protecting every customer who relies on the service. Once additional logs confirmed no other suspicious traffic, the laptop was released from isolation and the analyst went back to work—unaware how close a single click had come to triggering a serious security incident.
“The whole investigation—alert, DNSFilter pivot, user interview, fleet-wide block—took less time than a coffee break,” Matthew reflects. “Without the DNS logs, we’d still be sifting through EDR telemetry, hoping the payload hadn’t fired.”
The Results
Matthew’s DNSFilter policy blocked Malware outright and also denied any domain younger than 30 days (New) or 24 hours (Very New). That layering stopped the threat twice over: the two-day-old Greek site hosting the payload was already tagged Malware, and—even if that label had been missing—its age alone would have tripped the New-Domain rule. Because the console shows allowed and blocked queries side-by-side, Matthew could line up ordinary traffic with the suspicious hits and rebuild the two-minute timeline in a matter of minutes.
| Outcome | Detail |
| Payload Delivery | 0 bytes reached the endpoint (blocked by DNSFilter even though the DNS query came from the PowerShell, not a browser) |
| Employee Impact | No disruption; analyst returned to work immediately |
| Incident Response Time | < 30 minutes from alert to full containment and report |
| Fleet Protection | Staging domains blocked tenant-wide; AI classification protects all DNSFilter customers |
| False Positives | None during the investigation |
Matthew summarized the incident for the client’s leadership in a concise, two-page report—covering the DNS timeline, analyst statement, and proof of successful blocking—generated directly from DNSFilter’s CSV export.
Protection and Proof—All Through DNS
A quiet PowerShell alert could have marked the beginning of a credential-harvesting breach. Instead, DNSFilter intercepted the payload upstream and gave Matthew Chambers the visibility to trace the threat—before a single password ever left the network.
“DNSFilter gave me the evidence, the containment switch, and the audit trail—all in one place,” Matthew says. “That’s how incident response ought to feel.”
For FixFinder and its research-heavy client, the episode reinforced a simple truth: When analysts live on the open web, AI-powered DNS threat and content filtering isn’t just the first line of defense—it’s often the last, and the only thing standing between a benign blip and a full-scale compromise.

Tech Team Solutions
How one MSP gains long-term peace of mind when using DNSFilter for their cybersecurity protection.

DNSFilter vs Cisco Umbrella
Download this report to see how DNSFilter compares to Cisco Umbrella in security.
Customers love us, threats hate us







.png?width=154&height=50&name=fresno%20(1).png)














